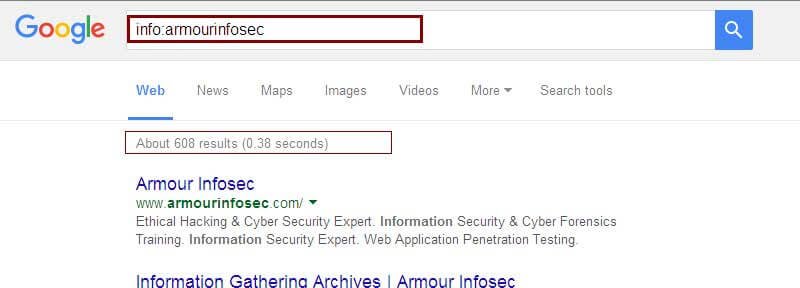
Hey ,
I'm MahaKaaL . And you known me. Today i'ill telling you What Is Google Hacking?
History of Google Hacking?
The concept of "Google Hacking" dates back to 2002,when Johnny Long began to collect interesting Google search queries that uncovered vulnable systems and sensitive information disclosures.
The list of google Dorks grew into large dictionary of queries,which were eventually organized into the original Google Hacking Database (GHDB) in 2004. These Google hacking techniques were the focus of a book released by Johnny Long in 2005 called Google Hacking for Penetration testers.
Since its heyday,the concepts explored in Google Hacking have been extended to other search engines , such as Bing and Shodan. Automated attack tools use custom search dictionaries to find vulnerable system and sensitive information disclosures in public system that have been indexed by search engines.
For a full visual timeline, delailing the major events and developments in Google Hacking from 2002 to present , see the Google Hacking History by Bishop Fox.
What Is Google Hacking??
Google hacking involves using advanced operators in the Google search engine to locate specific strings of text within search results. Some of the more popular examples are finding specific versions of vulnerable Web applications. The following search query would locate all web pages that have that particular text contained within them.
There are two types of Google operators:-
- Basic Operators
- Advance Operators
Basic Operators: -(+, -, ~, ., *, “”, OR)
“ + ” (It force inclusion of something common)
Using “+”It forces Google to search for a particular keyword. Its includes all web pages where both keywords occur. Do not put a space after the “+”.
Example: Smartphone +apple
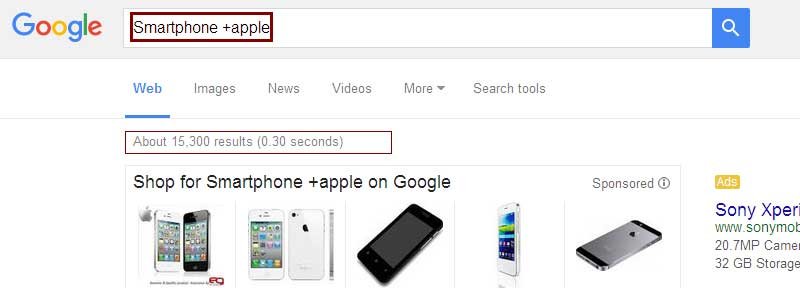
The minus operator does reverse. It gives you search results without the keyword placed after the operator. Do not put a space after the “–“
Example: Smartphone -apple
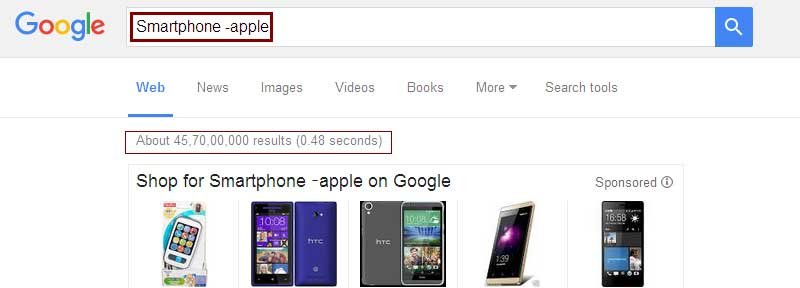
The tilde symbol generally suggests ‘similar to’.
Example: ~Smartphone apple
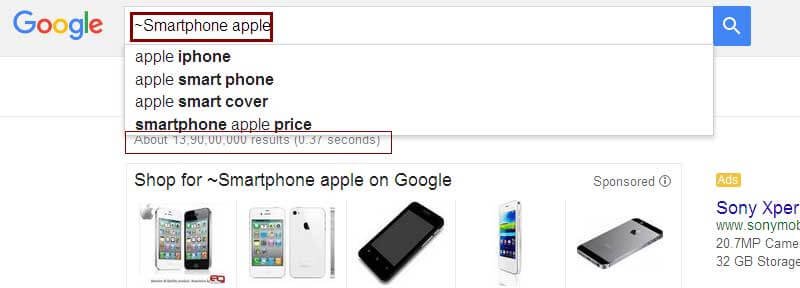
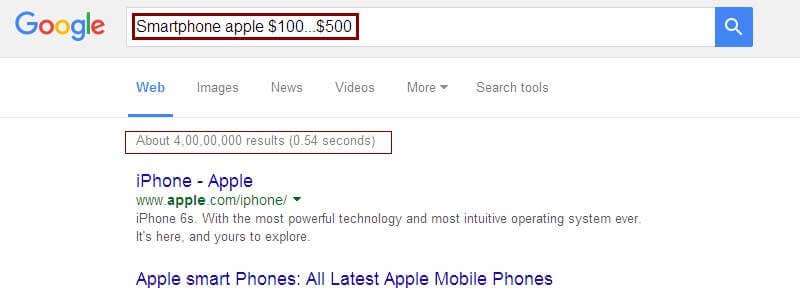
double dots help you to search within a range of two numbers.
Example: Smartphone apple $100…$500
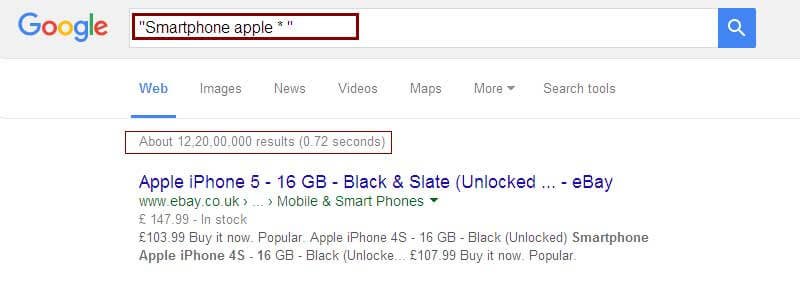
Asterisk operator (*) is handy when you are sure of more keywords are missing.
Example: “Smartphone apple * “
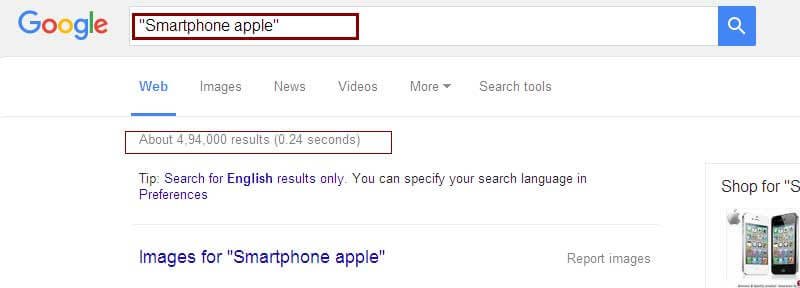
Surround a word or a phrase with double forces Google to search for pages that contain it exactly in the same form.
Example: “Smartphone apple”
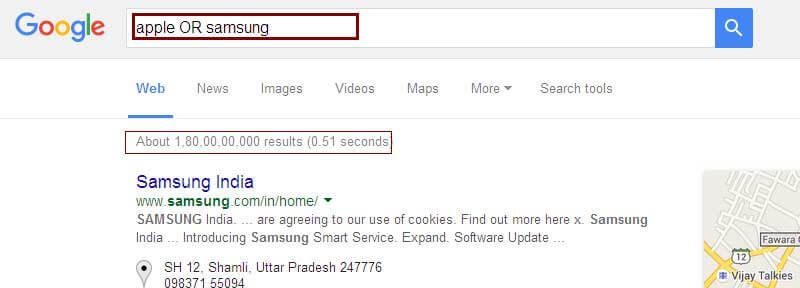
Using OR (in uppercase) with two or more keywords tells Google to search for pages that contain either of the words.
Example: apple OR samsung
Advance Operators?
| Operator | Purpose | Mixes with Other Operators? | Can be used Alone? | Web | Images | Groups | News |
|---|---|---|---|---|---|---|---|
| intitle | Search page Title | yes | yes | yes | yes | yes | yes |
| allintitle[3] | Search page title | no | yes | yes | yes | yes | yes |
| inurl | Search URL | yes | yes | yes | yes | not really | like intitle |
| allinurl | Search URL | no | yes | yes | yes | yes | like intitle |
| filetype | specific files | yes | no | yes | yes | no | not really |
| intext | Search text of page only | yes | yes | yes | yes | yes | yes |
| allintext | Search text of page only | not really | yes | yes | yes | yes | yes |
| site | Search specific site | yes | yes | yes | yes | no | not really |
| link | Search for links to pages | no | yes | yes | no | no | not really |
| inanchor | Search link anchor text | yes | yes | yes | yes | not really | yes |
| numrange | Locate number | yes | yes | yes | no | no | not really |
| daterange | Search in date range | yes | no | yes | not really | not really | not really |
| author | Group author search | yes | yes | no | no | yes | not really |
| group | Group name search | not really | yes | no | no | yes | not really |
| insubject | Group subject search | yes | yes | like intitle | like intitle | yes | like intitle |
| msgid | Group msgid search | no | yes | not really | not really | yes | not really |
intitle:- Restricts your search to the titles of web pages and provide exact result.
Example:
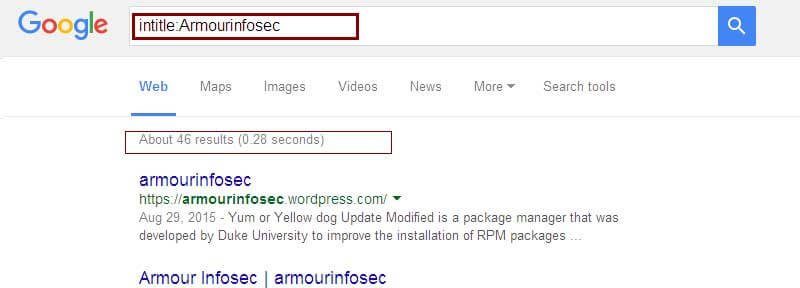
allintitle:- Find pages where in all word specified make up the title of the web page.
Example
allintitle:Armourinfosec
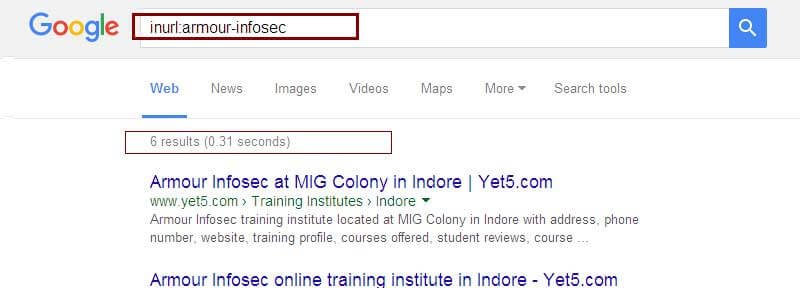
inurl : Restricts your search to the URLs of web pages.
inurl :armour-infosec
inurl:password
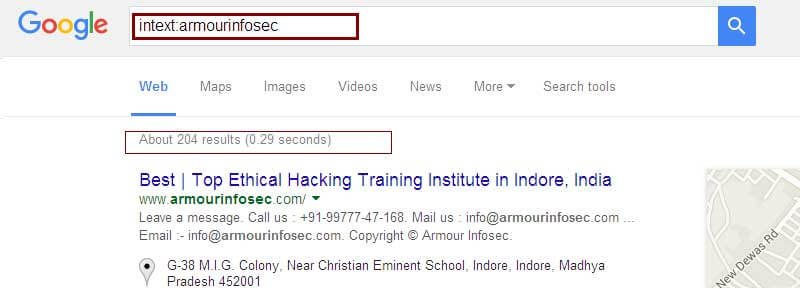
intext :- searches only in body text and provide text results according to your search query (i.e., ignores link text, URLs, and titles).
Example:
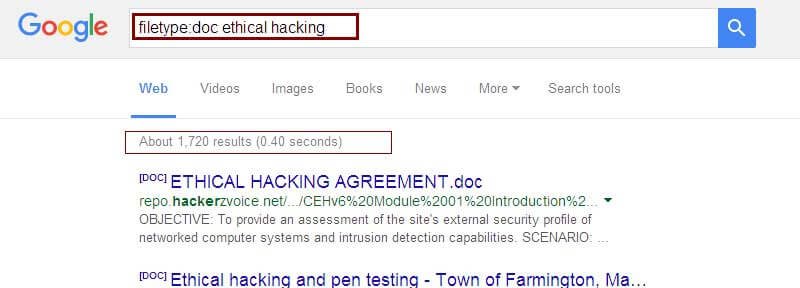
filetype :- Search for thesuffixes’ or filename extensions. These are usually, but notnecessarily, different file types.
Example:
site:- It allows the user to narrow your search by either a site or a top-level domain.
Example:
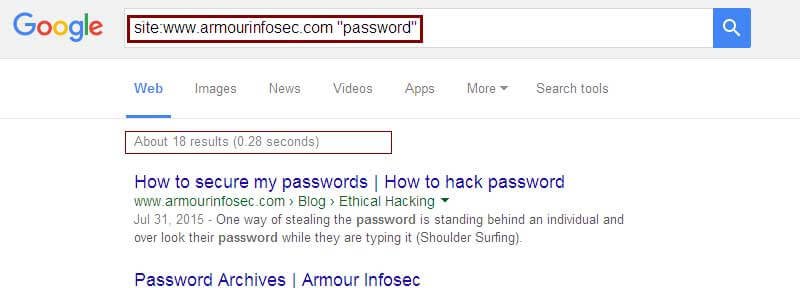
inanchor:- searches for texts in a page of link anchors. A link anchor is a descriptivetext of a link.
Example:
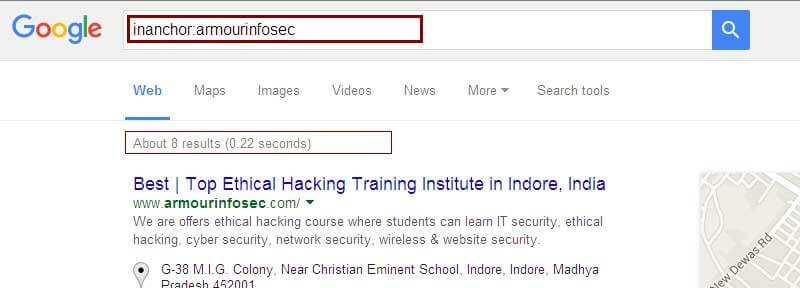
link:- It giveslisting of pages those which are linked to a specified URL.
Example:
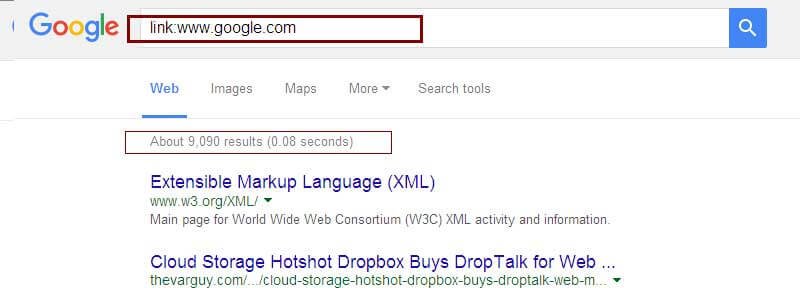
cache:- It finds a copy of the page that Google indexed and it give exact date and time.
Example:
related:- It finds those pages which are related to the specified page.
Example:
Google Hacking techniques?
- Exploring title messages from servers, e.g. intitle:"Welcome to IIS 4.0" You can see the results here. This is a list of servers running what is in the message, in the case IIS 4.0.
- Exploring server messages in the URL, e.g."VNC Desktop" inurl:5800 You can see the results here. This is a list of servers running VNC in port 5800 (we will study VNC as a remote control software and its vulnerabilities later in the course).
- Exploring filetype to find servers with FrontPage vulnerabilities, e.g. filetype:pwd service Note that pwd is not one of the types listed above, but Google still looks for service.pwd and you can see the results here. This is a list of usernames and encrypted passwords. As we will study later in the course a hacker can use John the Ripper to crack the password using brute force. The damage here is defacing a Web site, but users tend to repeat username and passwords elsewhere.
- Exploring filetype and inurl to find password files in servers, e.g. filetype:bak inurl:"htaccess|passwd|shadow|htusers" and you can see the results here. This is a list of usernames and encrypted passwords for login in servers. The damage here can be devastating, if the root password is available, as in one case it is. We will discuss UNIX/Linux vulnerabilities, the use of shadow passords, etc, later in the course.
- Exploring filetype, inurl and intext to find DB passwords, e.g. filetype:properties inurl:db intext:password and you can see the results here. This is a list of files containing username and password in databases. Once more you can see the root password, and in one case is blank!?!?
- Exploring security vulnerability scanners' output, not even using operators, e. g. "This file was generated by Nessus" and see the results here. This is a list of vulnerabilities found in servers generated by the Nessus scanner that were not deleted from the servers after it was run. The hacker has the vulnerabilities identified for him/her ...
By: MahaKaaL